Your cart is currently empty!
Practice Lab for CompTIA CySA+ CS0-003
Improve your practical IT skills in a live-lab environment.
Practice Lab for CompTIA CySA+ CS0-003
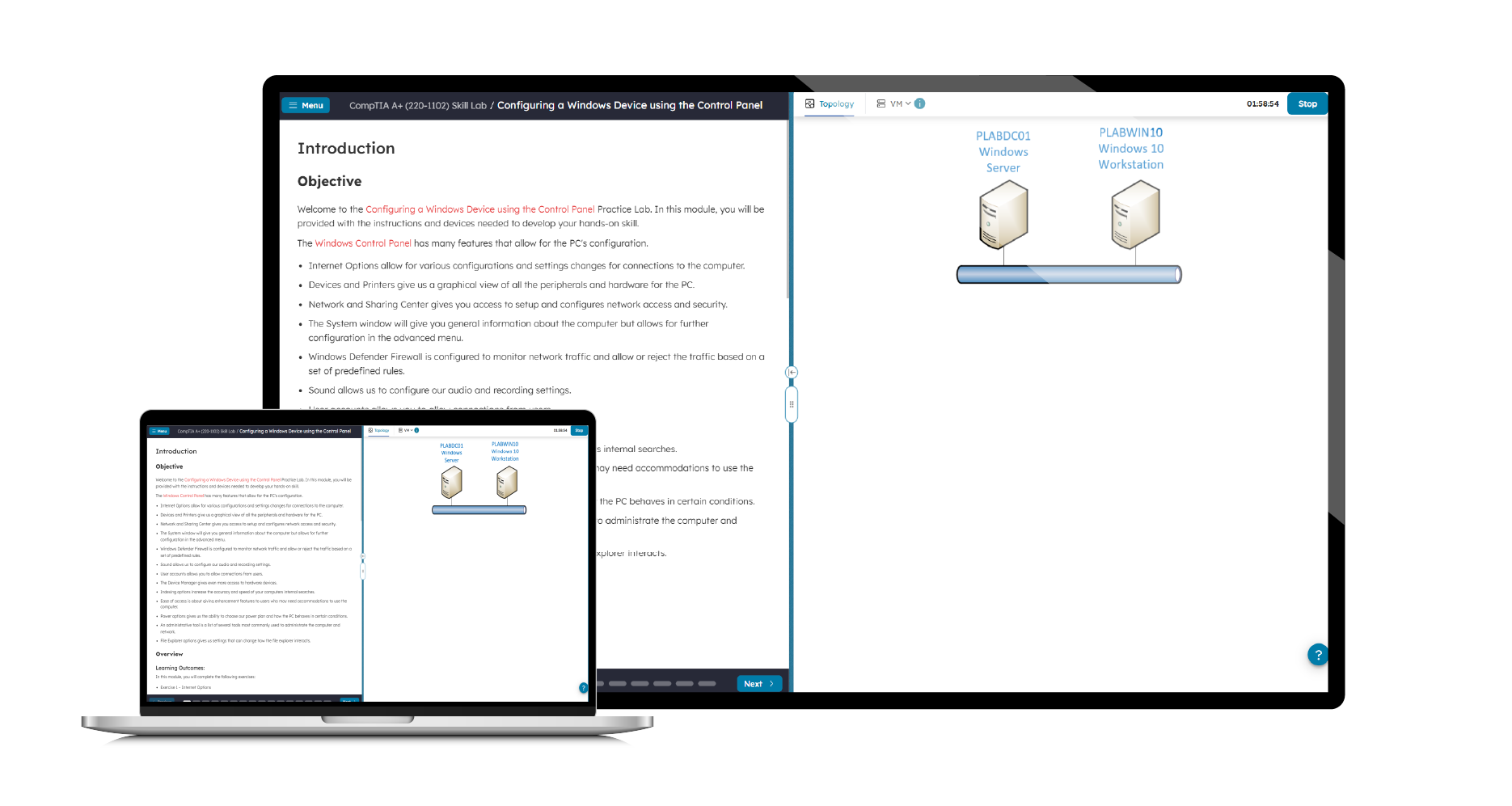
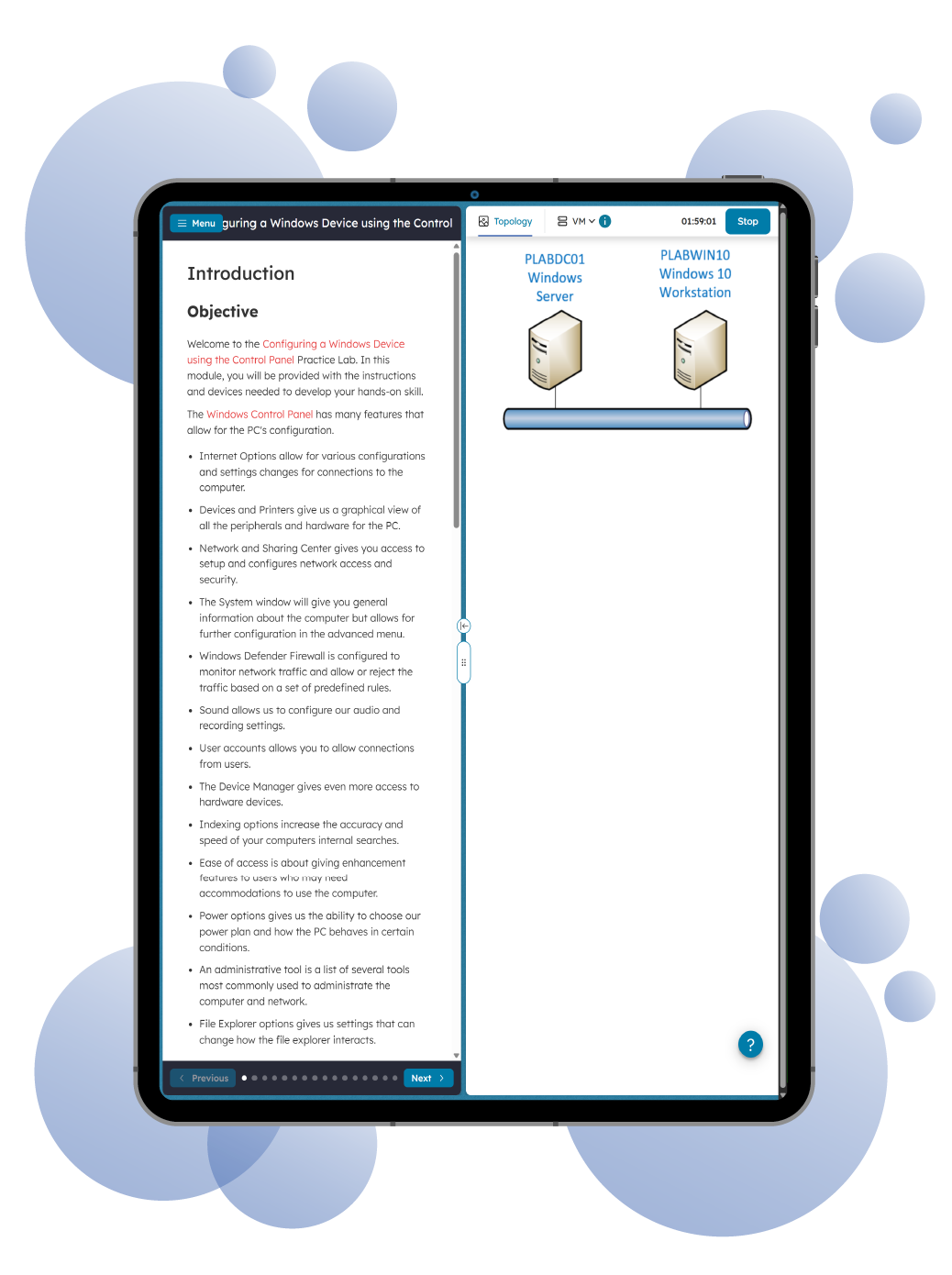
The CompTIA CySA+ CS0-003 Practice Lab will provide you with the necessary platform to gain hands-on skills in Cyber Security defense and Cyber Analytic techniques. By completing the modules, you will improve your practical skills in configuring and using threat detection tools, analyzing data, identifying vulnerabilities, identifying threats and risks securing and protecting applications and systems within an organization, as well as learning the impact of security and technological risks on various industries.
These same modules will help you understand the objectives and competencies required by the CompTIA CySA+ certification exam (CS0-003). CompTIA Cybersecurity Analyst (CySA+) is an intermediate certificate aimed at IT security analysts, vulnerability analysts, threat intelligence analysts, and IT professionals seeking to advance into the industry.
This Practice Lab focuses on the practical aspects of the exam objectives, although it also includes theoretical concepts that are not based in the lab environment. Although no prior hands-on experience is required to use or complete this Practice Lab, we assume that you know how to use a computer and that you are familiar with basic networking technologies and information security concepts.
CySA+ CS0-003
About the Exam
What is CySA+ CS0-003?
The CompTIA Cybersecurity Analyst (CySA+) certification verifies that successful candidates have the knowledge and skills required to detect and analyze indicators of malicious activity, understand threat intelligence and threat management, respond to attacks and vulnerabilities, perform incident response, and report and communicate related activity.
What topics are included in this exam?
- Security Operations
- Incident Response and Management
- Vulnerability Management
- Reporting and Communication
PRACTICE LABS
Course Modules
- System & Network Security Implementation Concepts
- Threat Intelligence & Threat Gathering Concepts
- Techniques to Determine Malicious Activity
- Vulnerability Scanning Tools & Techniques
- Identifying & Analyzing Malicious Activity
- Tools for Identifying Malicious Activity
- Attack Methodology Frameworks
- Vulnerability Data Analysis and Prioritization
- Incident Response Management Techniques
- Incident Response Communication & Reporting
- Vulnerability Reporting Concepts
- Vulnerability Patching & Attack Surface Management
Additional Resources
RELEVANT PRODUCTS
Shop similar products
-
Practice Lab
Practice Lab for CompTIA CySA+ CS0-003
-
Practice Lab
Practice Lab for CompTIA A+ 220-1102
-
Practice Lab
Practice Lab for CompTIA IT Fundamentals+
-
Practice Lab
Practice Lab for CompTIA Linux+ XK0-005