Your cart is currently empty!
Practice Lab for Ethical Hackers
Improve your practical IT skills in a live-lab environment.
Practice Lab for Ethical Hackers
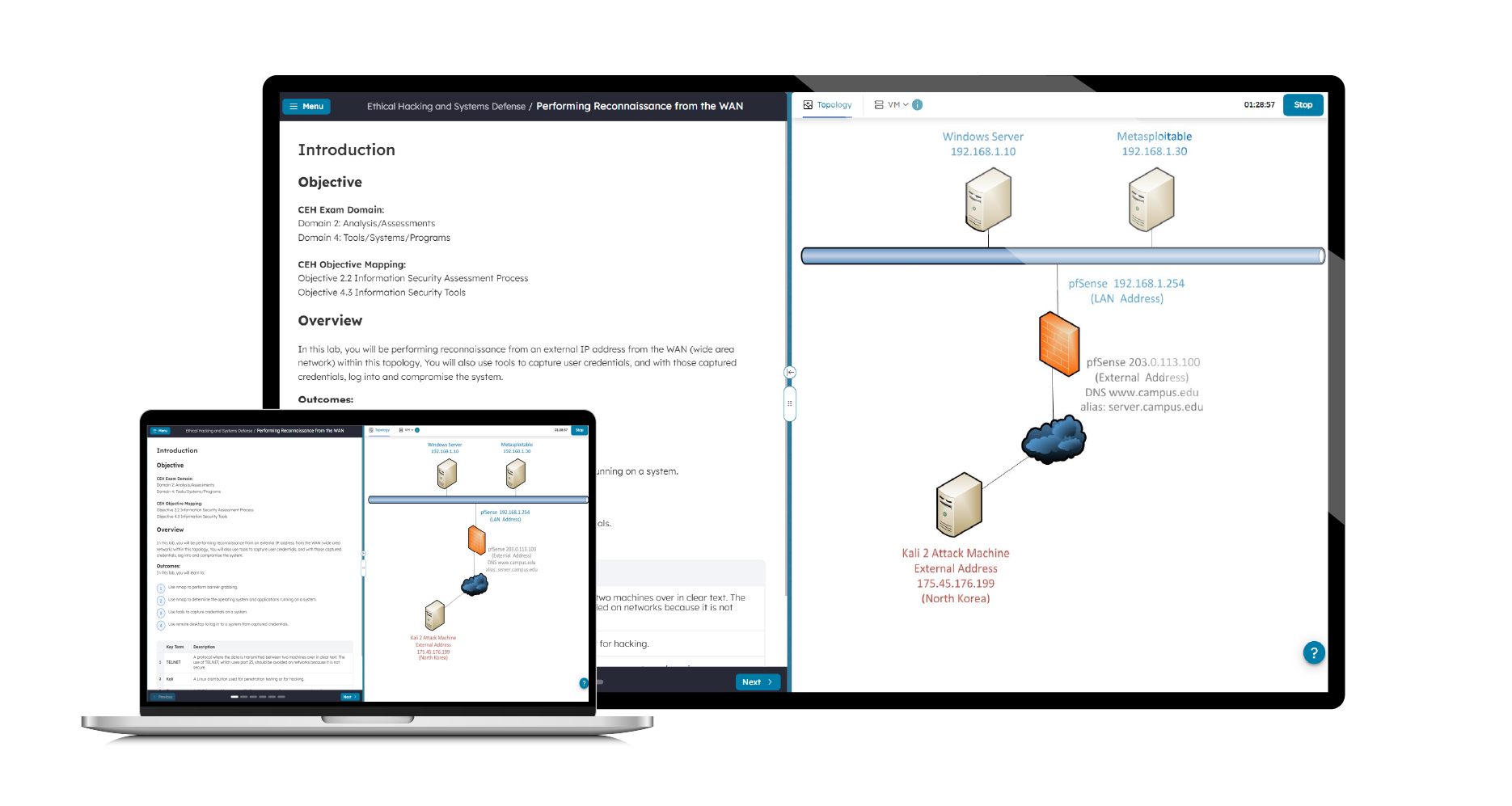
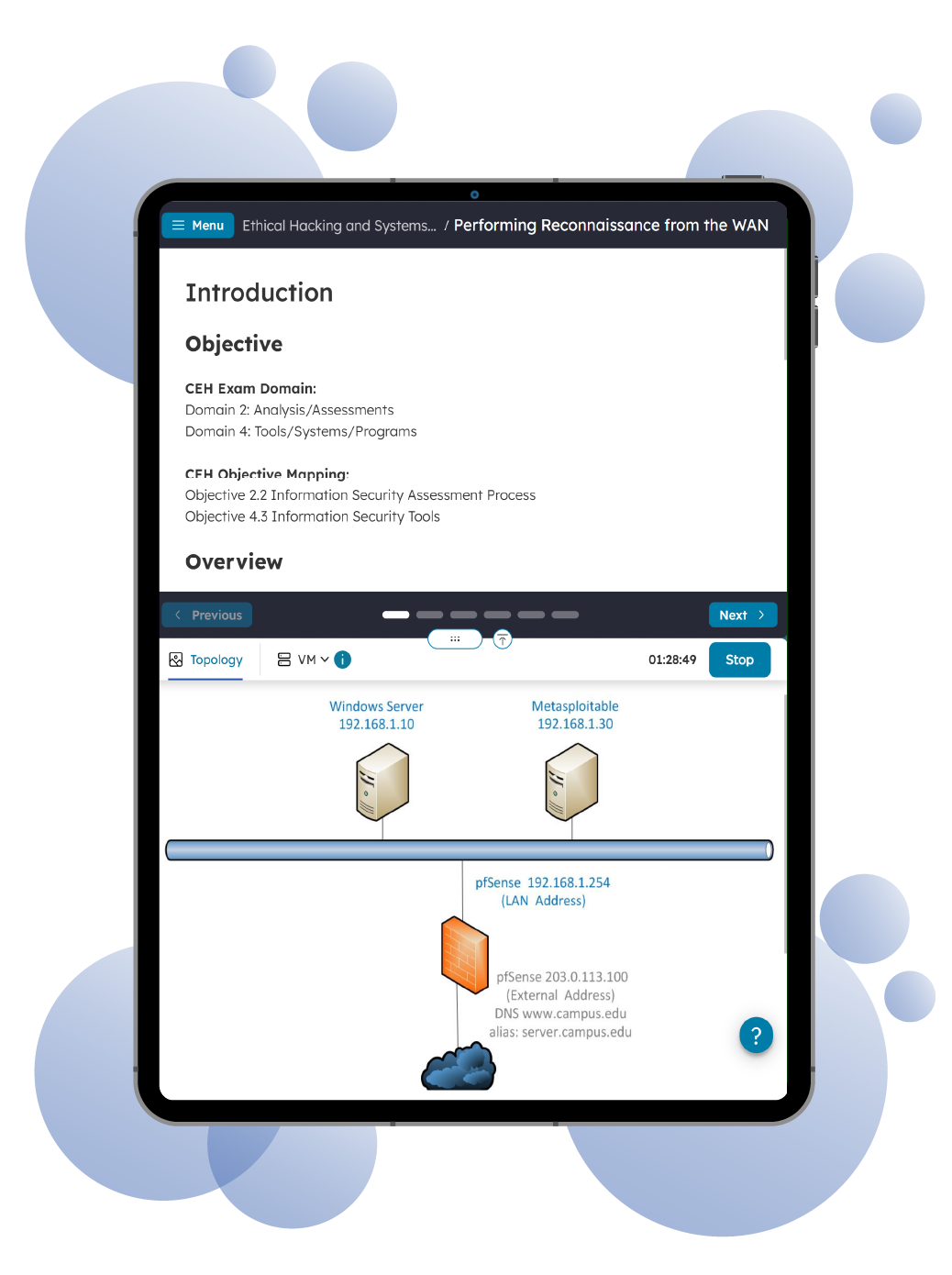
The Practice Lab for Ethical Hackers provides a dynamic environment where you can develop and refine the practical skills required for ethical hacking and penetration testing. Designed for hands-on learners, this lab delivers an immersive experience to help you understand how to identify, exploit, and mitigate vulnerabilities in a controlled and secure setting.
With step-by-step instructions and access to a preconfigured virtual network, you’ll perform tasks to improve your practical skills in Footprinting & Reconnaissance, Scanning Networks, Device & Device Enumeration, Social Engineering, System Hacking Concepts and Port & Process Monitoring. The lab environment eliminates the need to build or manage your own infrastructure, allowing you to focus entirely on skill development.
This lab is ideal for learners preparing for ethical hacking certifications, cybersecurity roles, or anyone seeking to strengthen their offensive security knowledge. While not tied to a specific exam, the content supports key competencies covered in certifications like CEH (Certified Ethical Hacker).
Certified Ethical Hacker, CEH, and EC-Council are registered trademarks of International Council of E-Commerce Consultants DBA EC-Council. ExSim-Max for Ethical Hacking is independently developed and is not affiliated with, nor has been sponsored or approved by EC-Council. All third party trademarks and/or registered trademarks referenced are the property of their respective owners.
312-50 Ethical Hacking
About the Exam
What is 312-50 Ethical Hacking?
The exam required for EC-Council’s Certified Ethical Hacker (C|EH)® certification will test the understanding and knowledge of weaknesses and vulnerabilities in target systems. To be eligible to apply to sit for the CEH (ANSI) exam, a candidate must either:
- Have a minimum of 2 years work experience in InfoSec domain, or
- Have attended an official EC-Council training.
- Earn 120 EC-Council Continuing Education (ECE) credits within a three-year period.
- Earn a minimum of 30 credits per year.
- Participate in the ECE program.
What topics are included in this exam?
- Information Security and Ethical Hacking Overview
- Reconnaissance Techniques
- System Hacking Phases and Attack Techniques
- Network and Perimeter Hacking
- Web Application Hacking
- Wireless Network Hacking
- Mobile Platform, IoT, and OT Hacking
- Cloud Computing
- Cryptography
PRACTICE LABS
Course Modules
- Footprinting and Reconnaissance Techniques
- Network Reconnaissance Techniques
- Enumeration Reconnaissance Techniques
- Vulnerability Analysis Tools & Techniques
- System Hacking Methodologies
- Malware Threat Concepts
- Network Sniffing Techniques
- Social Engineering Exploits
- Denial of Service Attacks
- Session Hijacking Concepts
- Compromising Web Servers
- Web Application Hacking
- SQL Injection Methodologies
- Introduction to Cloud Computing
- Cryptography Techniques
Additional Resources
BUNDLE & SAVE
Bundle Products for Instant Savings
| Included Products | Price | |
|---|---|---|
|
|
$198
$179 / year
|
SAVE $19
|
RELEVANT PRODUCTS
Shop similar products
-
Practice Lab
Practice Lab for Ethical Hackers
-
Practice Exam
ExSim-Max for CISSP
-
Practice Exam
ExSim-Max for Ethical Hacking
-
Practice Lab
Practice Lab for CISSP